What is AAM security audit and how it works
In version 6.9.40 of free AAM plugin, we launched a powerful new feature called the "Security Audit". It is designed to scan your WordPress website for potential security vulnerabilities, including misconfigurations, elevated privileges, or incorrectly defined access controls. It is also aligned with best practices set by the WordPress core team, helping reduce confusion for website administrators. We engineered this feature based on thousands of real-world use cases we’ve encountered, ensuring it addresses the most common security pitfalls.
Why Security Audits Matter
The Security Audit service is an essential tool that website owners can use to periodically review and tighten their site’s security. It helps identify roles and users with elevated permissions, which could potentially be exploited to compromise your website. It also detects unguarded endpoints that might allow malicious applications to access sensitive data.
The audit is not just a one-time check. The AAM team continuously revises and improves the list of checks with each new version release, ensuring that you always stay ahead of potential security threats.
Key Features of the AAM Security Audit
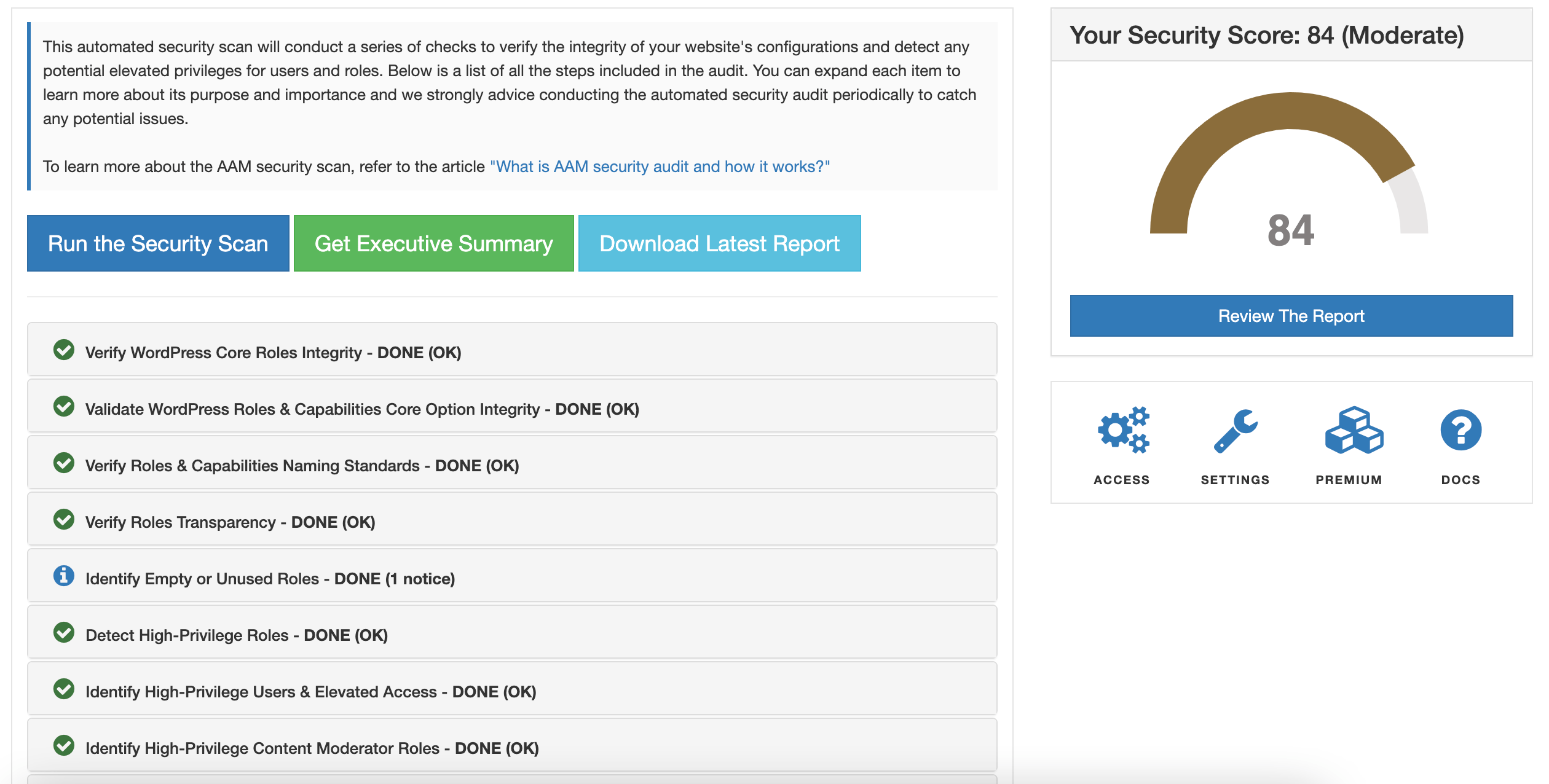
Here’s an overview of the current checks included in the latest release of the Security Audit service:
Verify WordPress Core Roles Integrity. Maintaining the integrity of WordPress core roles is essential. Altering or removing default roles can cause conflicts with plugins, lead to failed user registrations, and introduce security risks. This check ensures that the core roles remain intact, keeping your website stable and secure.
Validate WordPress Roles & Capabilities Core Option Integrity. The core _user_roles option manages WordPress roles and capabilities. Altering its structure can break functionality, introduce vulnerabilities, and complicate updates. This check ensures that role modifications adhere to WordPress’s built-in APIs and do not compromise the underlying structure.
Enforce Roles & Capabilities Naming Standards. Adhering to WordPress’s naming conventions for roles and capabilities is vital for maintaining consistency, reducing errors, and ensuring compatibility across plugins and themes. This check promotes best practices in naming to help improve security and collaboration.
Ensure Registered Roles Transparency. Hidden roles can obscure access controls and create security risks by making it difficult to audit user permissions. This check flags hidden roles, helping you ensure full transparency and control over user access.
Identify Empty or Unused Roles. Empty roles, which lack any assigned capabilities, can pose security risks if misused by plugins or themes. This check identifies such roles, enabling administrators to audit and remove them to avoid confusion and security vulnerabilities.
Detect High-Privilege Roles. Roles with high-level privileges carry significant risks. Users with access to core settings, file uploads, or theme/plugin management can introduce vulnerabilities or disrupt site functionality. This check flags high-privilege roles that may need review.
Identify High-Privilege Users & Elevated Access. Assigning high-privilege capabilities directly to users or expanding the number of users in high-privilege roles increases the potential attack surface. This check identifies users with elevated access to ensure that roles and capabilities are properly managed, minimizing security risks.
Identify High-Privilege Content Moderator Roles. Assigning high-privilege content moderation capabilities in WordPress, poses significant security risks if granted to untrusted roles. These capabilities allow users to manipulate or delete live content, inject malware, and harm SEO performance, potentially leading to data loss and compromised site integrity. By carefully managing user roles and permissions, you can protect your website from potential cyber threats while ensuring content integrity.
Flag Elevated Privileges for Core Roles. Modifying core WordPress roles like Editor or Subscriber by granting extra capabilities can lead to security vulnerabilities. This check ensures that core roles remain as intended and recommends creating custom roles for extended functionality.
Audit RESTful API Discovery Endpoint. The /wp-json/ endpoint, part of WordPress’s RESTful API, can expose sensitive information to unauthorized users. This check audits the API endpoint to ensure that access is properly restricted to minimize the risk of exploitation.
Audit XML-RPC Endpoint Access. The outdated XML-RPC endpoint can be a target for brute-force attacks and other exploits. This check assesses whether the endpoint is still enabled and recommends disabling it to strengthen site security.
Check Editable File System Permissions. Writable WordPress file systems can lead to malware injection or backdoor installation. This check ensures that critical directories, like /wp-content/plugins and /wp-content/themes, have read-only permissions to prevent unauthorized modifications.
Audit Results and Actionable Insights
After running the Security Audit, you’ll receive a detailed report categorizing all findings.
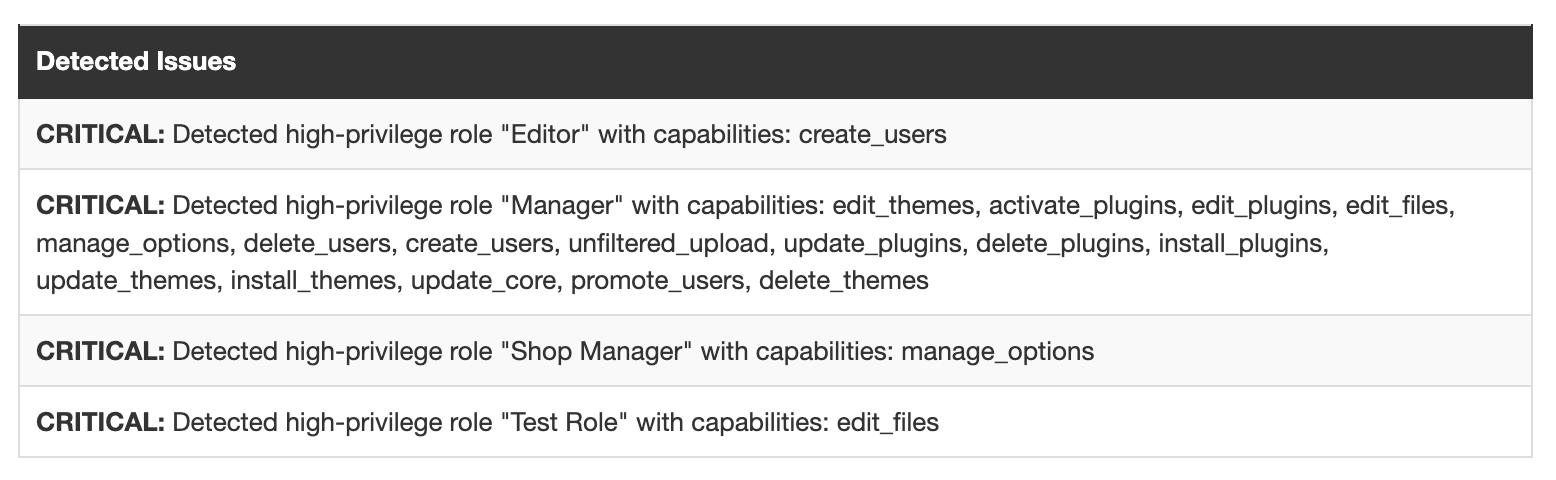
- Critical: Issues that pose significant risks to your website’s security or functionality. These should be addressed immediately.
- Warning: Not critical but important issues that require attention. It’s recommended to monitor these and resolve them as soon as possible.
- Notice: Issues that may not have an immediate impact but should be reviewed with your development team to improve security and align with best practices.
You have the option to receive a complimentary executive summary outlining the key issues found. Just click "Get Executive Summary" and confirm by selecting "Prepare My Executive Summary".
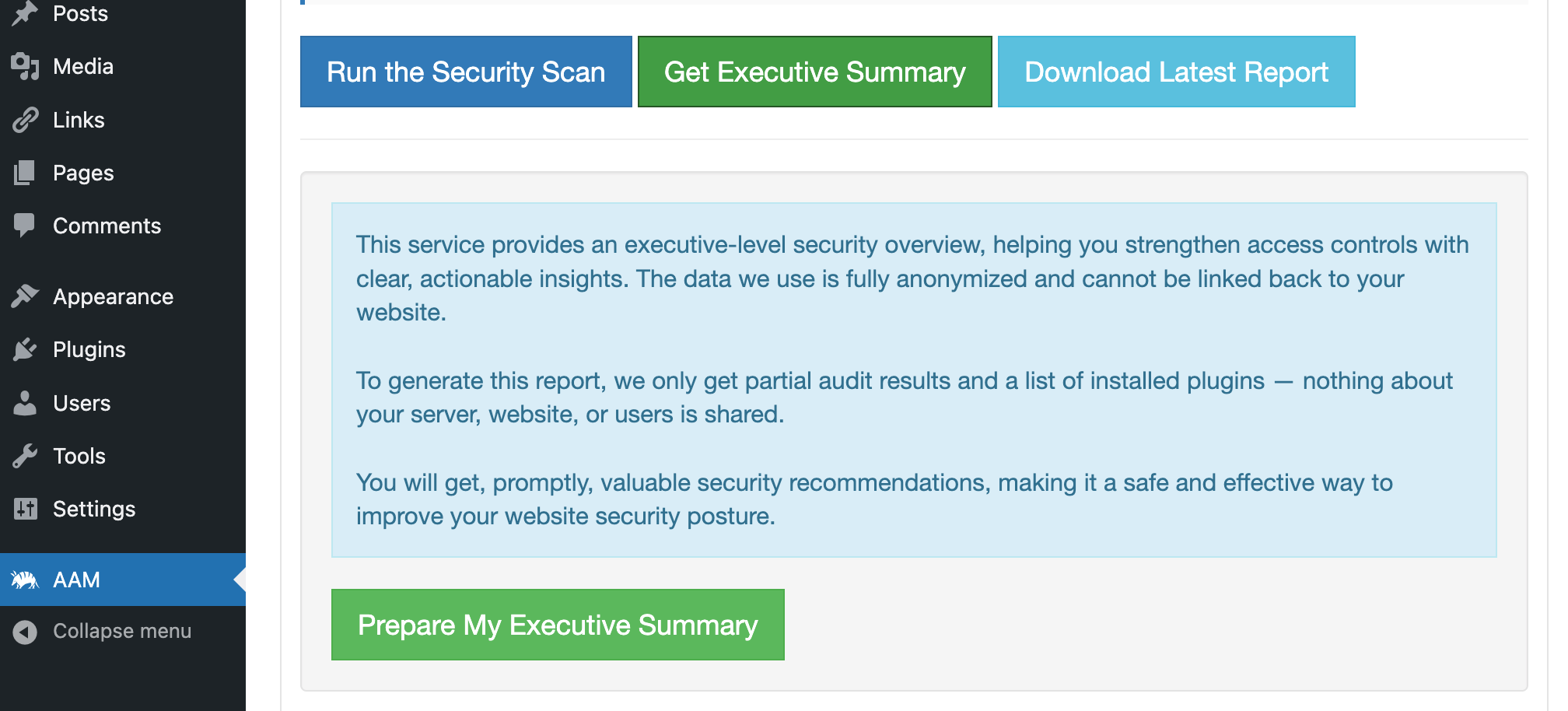
Within seconds, you'll receive a high-level overview of your current security posture, including bullet-pointed issues and actionable recommendations.
Conclusion
The AAM Security Audit service offers an invaluable safeguard for your WordPress website. While none of the identified issues necessarily indicate that your website is compromised, they highlight areas that can be improved to reduce the risk of future security breaches. With regular audits, you can proactively address vulnerabilities, secure elevated permissions, and align your site with the latest WordPress best practices.