Enhancing WordPress Security Beyond the Basics
When discussing WordPress security, the focus often falls on common preventive measures such as protecting against brute force attacks, DDoS attacks, setting up firewalls or Web Application Firewalls (WAFs), and scanning for malware or outdated plugins, themes or core. While these are critical components of securing any website, they only address external threats. What happens when a potential threat comes from within?
Imagine securing a house. You would install locks on doors and windows, set up security cameras, or even build a fence to protect it from intruders. These measures safeguard your home from external threats. But once you invite guests into your home, all these external security measures become irrelevant. If no boundaries are set inside your home, your visitors could wander freely, accessing areas you never intended them to.
This same principle applies to your WordPress website. Once a user is authenticated and gains access, the external security layers no longer apply. WordPress assigns roles to users, granting them the ability to perform certain actions on your site. This internal access control is often overlooked but crucial for maintaining security. Unlike external threats, internal security is highly specific to each website, and there’s no universal solution.
It’s up to you, as the site owner, to define boundaries for users with authenticated access. For example, you wouldn’t want a guest in your home to use your toothbrush or snoop through your private tax records. Similarly, you wouldn’t want users on your website to perform actions that go beyond their intended role. Without proper boundaries, authenticated users may inadvertently or maliciously access areas of your site you never intended them to.
Addressing Internal Security with Advanced Access Manager
The Advanced Access Manager (AAM) plugin for WordPress addresses this internal security gap. Recently, AAM introduced a new feature called Security Audit, designed to help site owners identify potential vulnerabilities in access control. This audit performs a series of checks on your website to detect any misconfigurations or suspicious user activity.
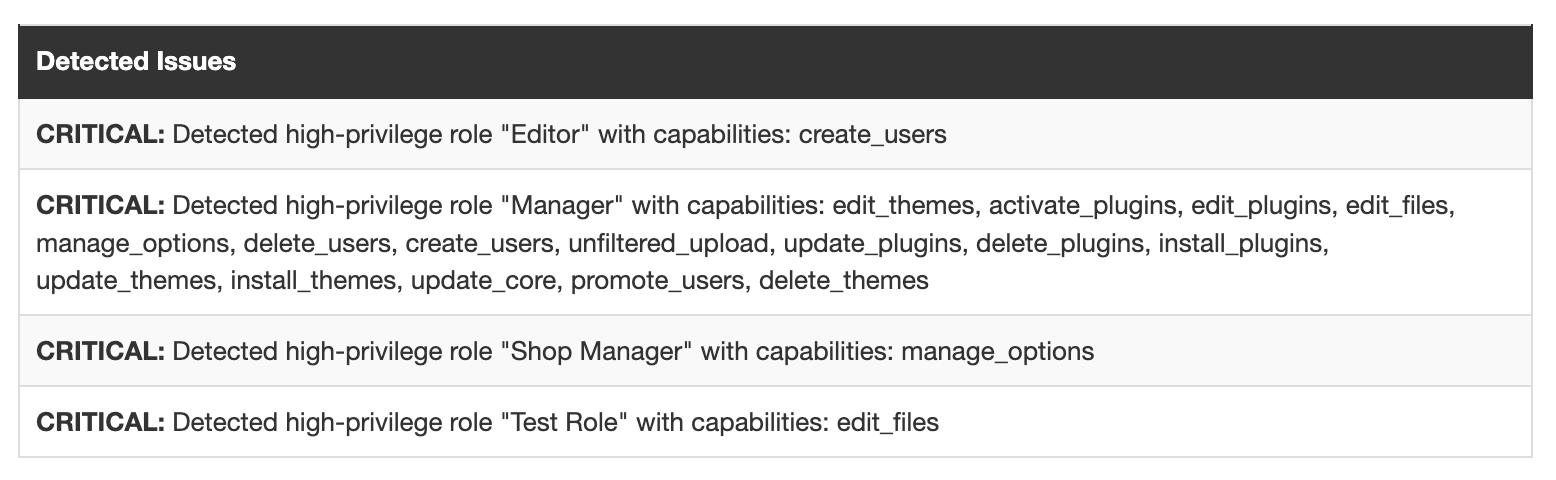
For instance, the audit examines whether any users or roles have been granted elevated access controls beyond what’s necessary. Elevated privileges, such as installing or activating plugins, modifying the file system, or creating and deleting users, can pose significant security risks if misused.
The Security Audit also checks for other important issues, including:
- Misconfigured WordPress core settings.
- Exposed RESTful API endpoints or outdated XML-RPC endpoints, which can be vulnerable to attacks.
- Editable file systems that can allow malicious actors to inject harmful code.
How the Security Audit Works
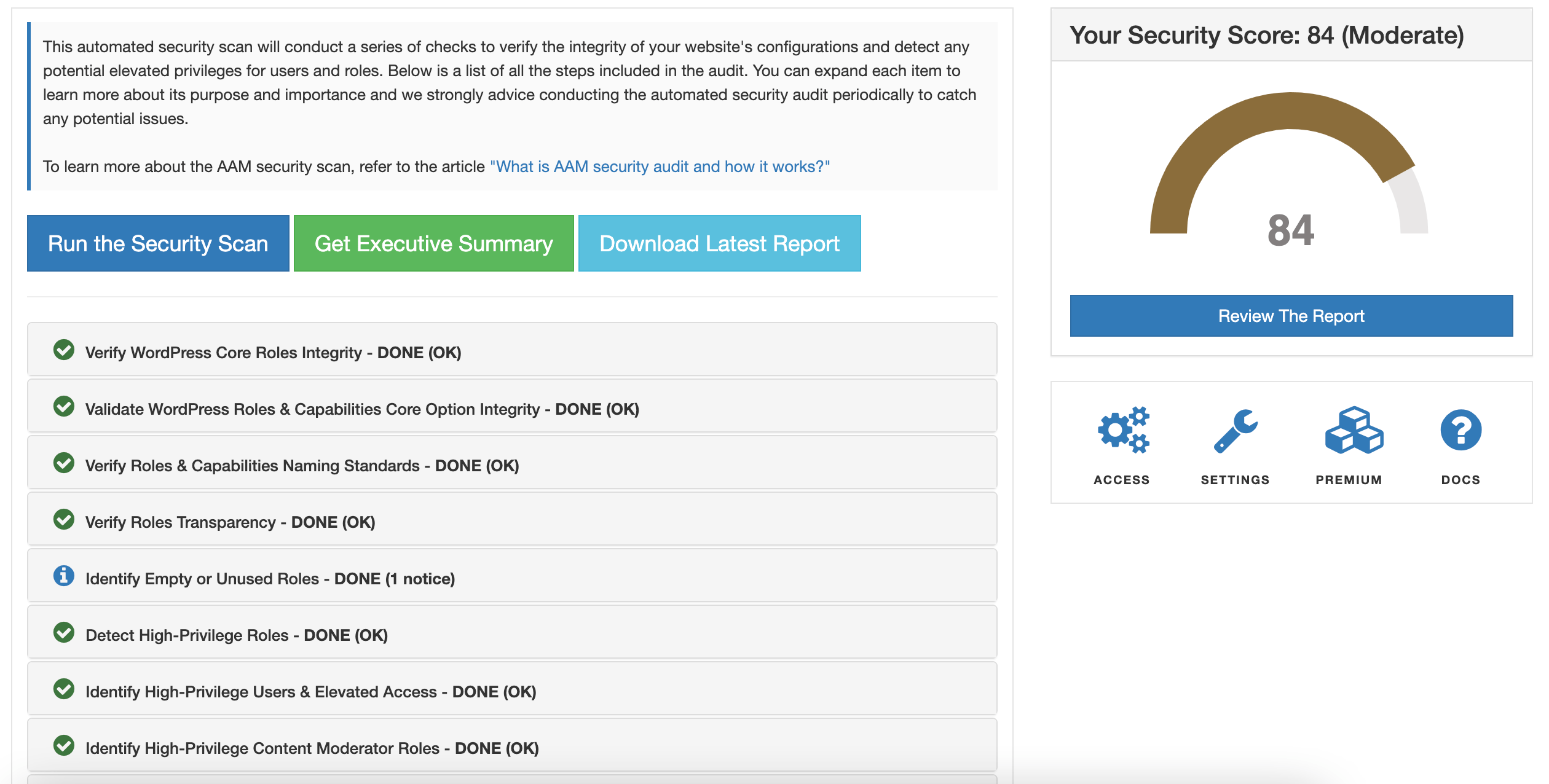
Using the Security Audit feature is simple. From the AAM page, click on the “Security Audit” button, and the system will perform all necessary checks. The results are displayed visually, highlighting areas that need your attention.
For example, the audit might flag any WordPress core roles that have been modified from their original state. Maintaining the integrity of these core roles is critical for site security, and AAM provides resources on why it’s important not to tamper with them.
Other checks include ensuring WordPress options haven’t been corrupted, enforcing role and capability naming standards, and verifying that essential core roles haven’t been deleted. These issues are common, especially with the wide range of plugins and themes available, many of which don’t adhere to WordPress core standards.
Mitigating Security Risks
One of the most significant risks uncovered by the Security Audit is the over-assignment of administrative roles. Many WordPress sites have an excessive number of administrators or users with unnecessary elevated privileges, which can lead to serious vulnerabilities. Only a small, trusted group of users should have the power to make major changes, such as installing plugins or creating new users.
The audit also helps ensure that legacy APIs like XML-RPC, which are no longer widely used, are disabled. Keeping these APIs enabled unnecessarily creates additional entry points for attackers.
Finally, the audit flags any issues with the file system. An editable file system can be a dangerous backdoor for malicious actors, allowing them to inject harmful code that could compromise or even destroy your website.
Next Steps
After running the audit, if you’re unsure about how to address any issues, AAM provides extensive resources on their website. You can also schedule a consultation with the AAM team to guide you through the necessary steps to improve your website’s security posture.
Securing a WordPress site is about more than just defending against external threats. With the right tools and practices, you can protect your site from within by managing user roles and access controls effectively. The AAM Security Audit is an essential tool for taking your WordPress security to the next level.
By adopting a comprehensive approach to WordPress security, you can ensure that both external and internal threats are properly managed, keeping your website safe and secure.