There is something wrong with WordPress application passwords
By default, WordPress allows all users, including the lowest-level subscriber role, to create application passwords. While this might seem harmless, it’s a security loophole that can expose your site to unnecessary risk.
What are application passwords?
Alright, you may wonder - what is an application password? In short - this is a random string that is used to authenticate API requests; or as you might already guessed - highly technical thing.
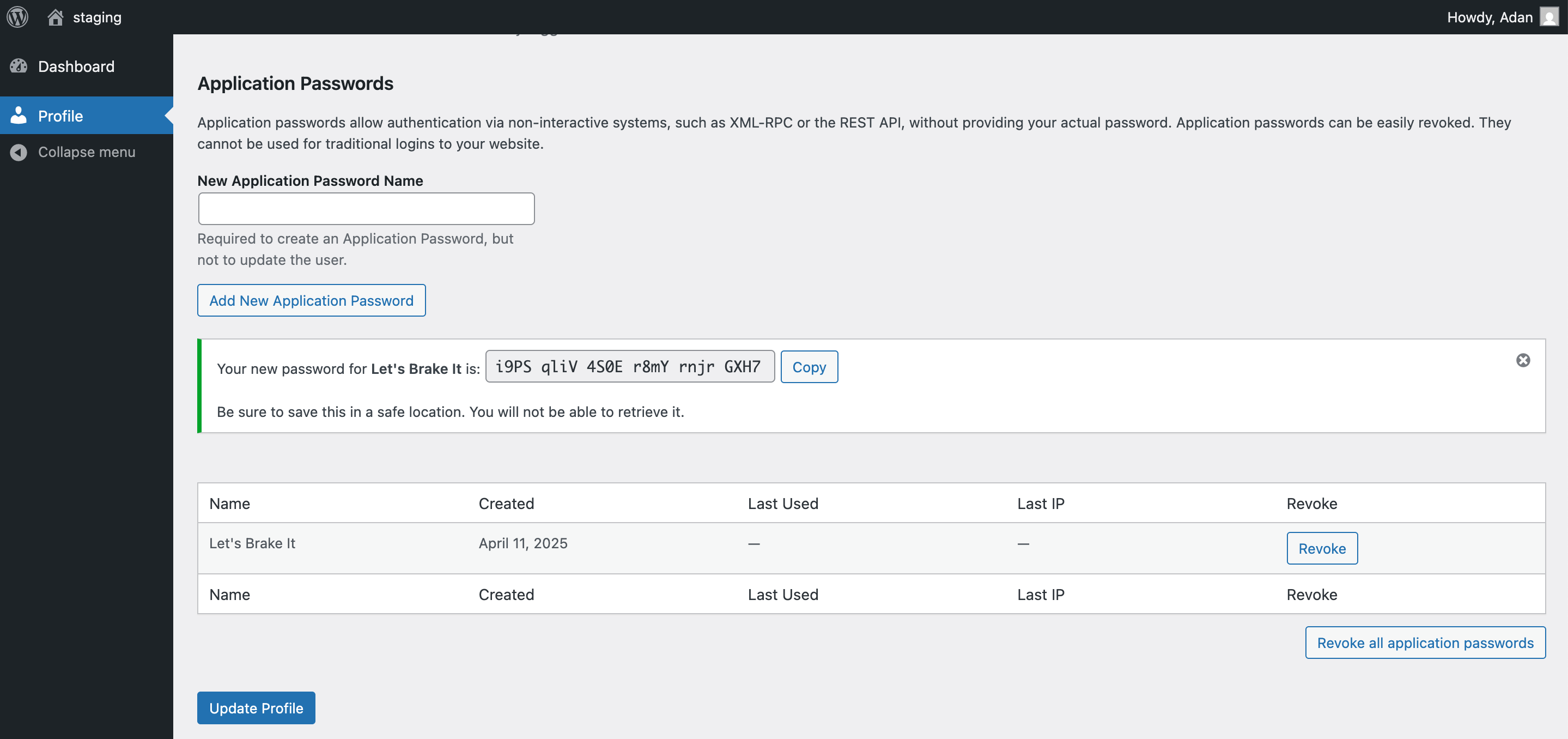
Application passwords are persistent credentials that allow access to the WordPress REST API without needing to log in through the regular admin interface. They bypass CAPTCHA, 2FA and login rate limiting.
So, why is this a problem?
Mostly, you may require user registration to allow to read gated content, maintain a user profile, collaborate with other users, leave comments, etc. In most cases, your user never need persistent API access.
Allowing them to create application passwords means:
- Anyone can plug those credentials into automated REST API scanners.
- Malicious users can enumerate endpoints and probe for vulnerabilities.
- These passwords don’t expire unless manually revoked.
- Some plugins or themes might expose data based on poor access checks.
This opens your site to reconnaissance, which is often the first step in a targeted attack. So, the bottom line - your users don’t need API access. Don’t give them persistent credentials that can be abused. Lock it down.
How to mitigate?
Surprisingly, WordPress core doesn’t offer a straightforward way to disable application passwords. But with Advanced Access Manager (AAM) version 7, you can take full control.
In this major release, we introduced the custom capability aam_manage_application_passwords. This capability:
- Blocks programmatic creation of application passwords.
- Hides the "Application Passwords" section from user profile pages.
- Restricts direct access to
/wp-admin/authorize-application.php, which can otherwise be used to create application passwords.
To disable the application passwords feature, simply:
- Ensure you’re using AAM version 7 or higher.
- Open the AAM dashboard and switch to managing the Administrator role.
- Go to the "Capabilities" tab and create the custom capability
aam_manage_application_passwords.
That’s it. Now, only users with this capability (in our case only administrators) can create or manage application passwords. Need to allow it for specific roles or users? Simply assign the capability via the "Capabilities" tab.