Users & Roles Governance
Proper tools for governing users and roles visibility, as well as defining who can manage users, roles and how, are essential for several security reasons.
WordPress core provides some powerful capabilities, which we'll cover later. However, AAM (Advanced Access Manager) enhances these by offering fine-tuned access controls based on user/role levels, protecting individual users from those with higher privileges.
WP Core Capabilities
WordPress core includes several capabilities to manage users:
create_users: Create new users.list_users: View the list of users via the "All Users" admin page or through the RESTful API.edit_users: Edit any user.delete_users: Delete any user.remove_users: Remove any user from a site in a multi-site setup.promote_users: Change any user's role.
While these capabilities are effective, they do not address scenarios such as granting elevated access to freelancers, developers, or customer support agents without risking changes to your admin user, or allowing certain roles to list users without seeing high-privilege users.
This is where AAM's "Users & Role Governance" (aka Identity Governance) service becomes essential.
Introduction to the UI
In AAM version 7.0.0, the "Identity Governance" tab lets you define governance rules for distinct identity types: "Users" & "Roles". In other words, you can define how any individual user or group or users (role) can see and manage other users and roles.
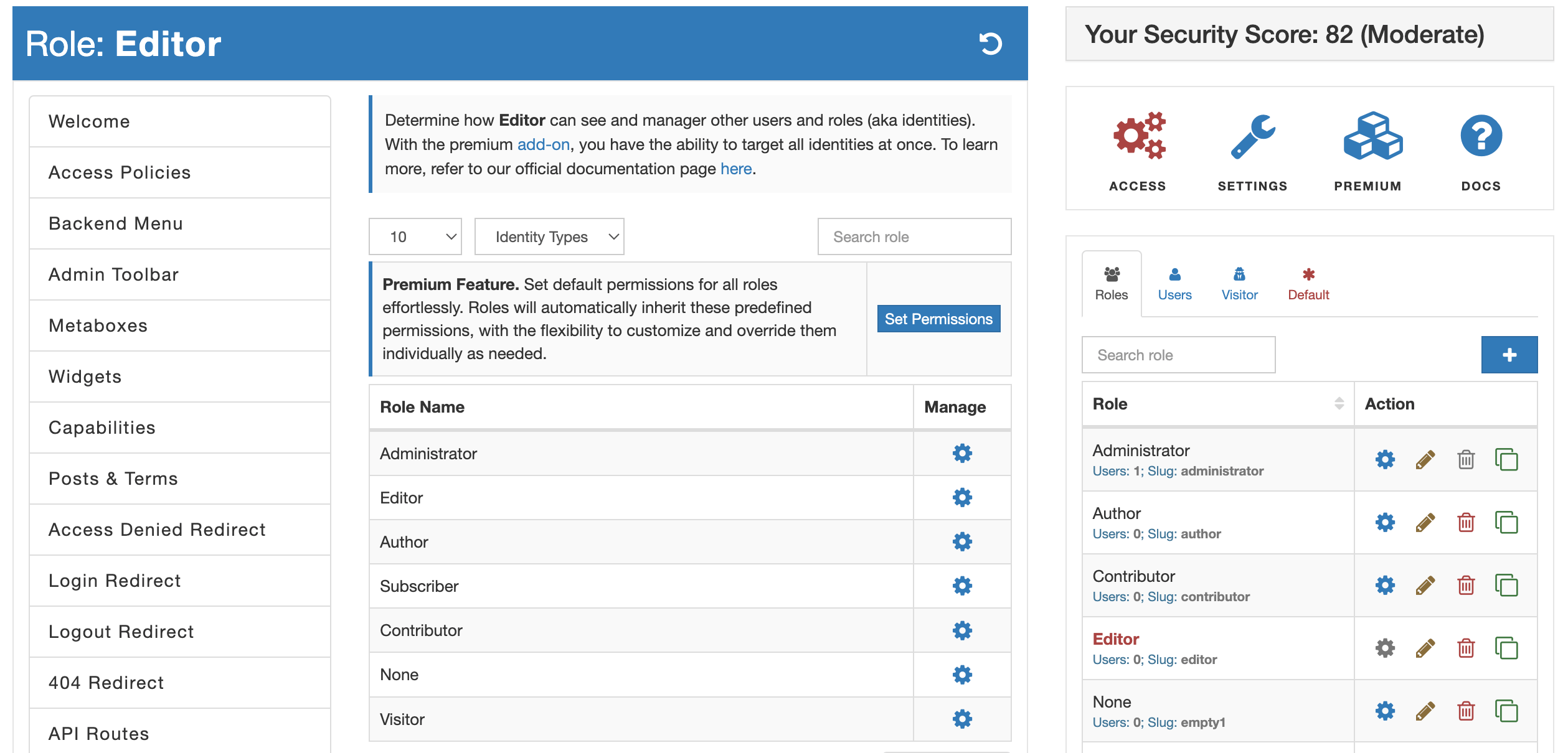
When you select the "Identity Governance" tab, you are immediately presented with the list of registered roles on your WordPress site. Here you can define how a selected access level can manage other roles. However, if you need to target a very specific user, you can switch between identity types by selecting a respectful option from the "Identity Types" dropdown.
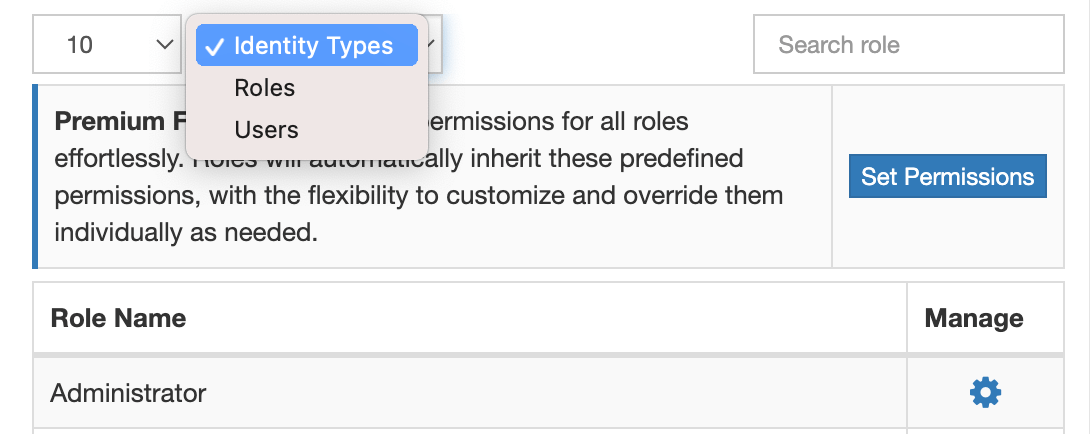
The premium add-on also offer the ability to define default access controls for all roles or users. For instance, let's say you want to delegate the ability to manage subscribers to a community manager in your organization. However, you only need to allow her to be able to manage users with Subscriber role. You can simply define a default access to all roles by hiding them but then override this only for the Subscriber role.
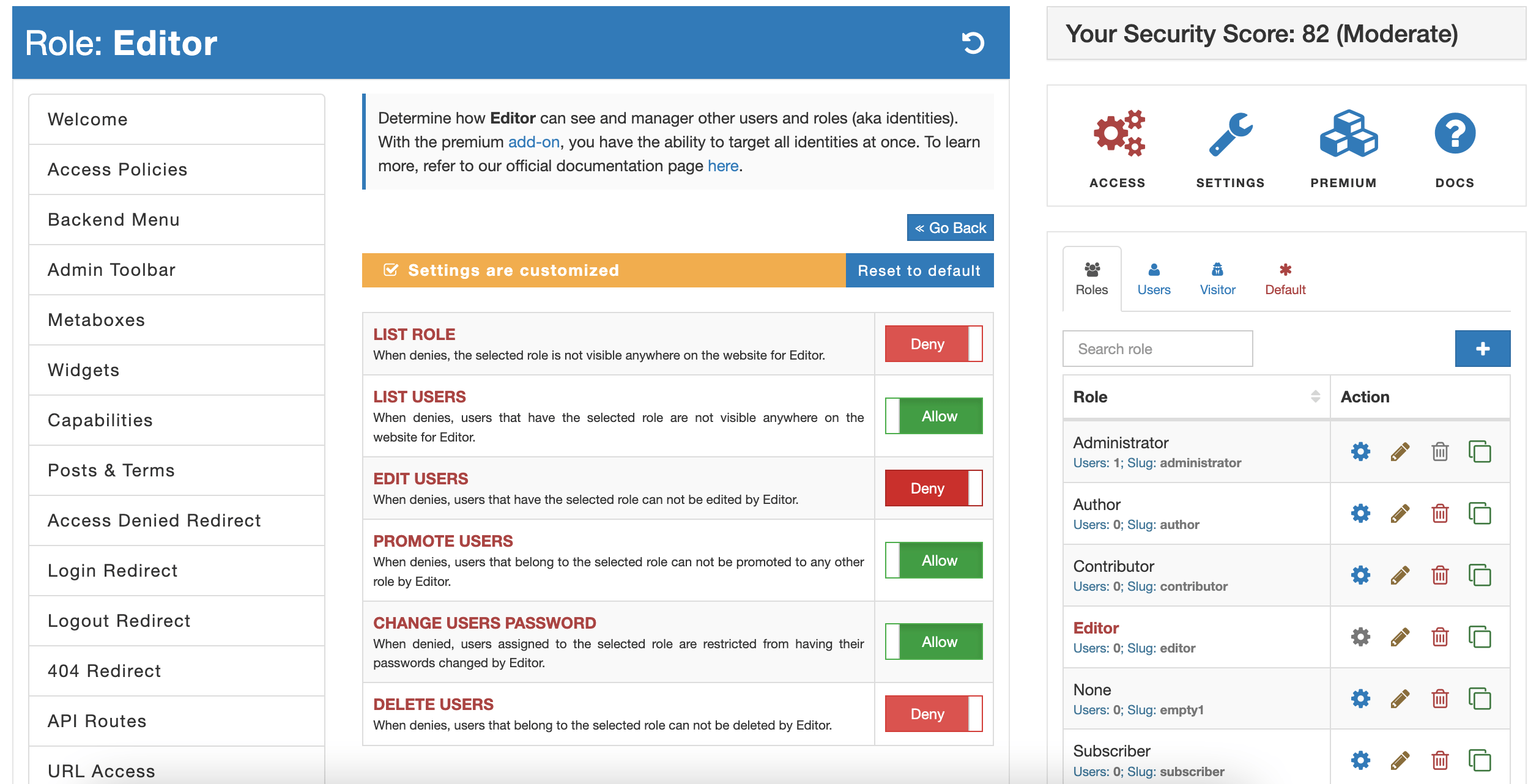
To define access controls for any role or user, you can select a gear button. This brings the access controls form with the list of permissions that varies depending on the identity type.
Access Policies Route
Alternatively, use AAM access policies to define rules using Role and Userresources.
Access policies provide greater flexibility with various conditions not possible through the UI. For instance, the following policy denies listing or managing users if the current user is not in Paris, France:
{
"Statement": {
"Effect": "deny",
"Resource": "User:*",
"Action": [
"List",
"Edit",
"Delete"
],
"Condition": {
"NotEquals": {
"Operator": "AND",
"${GEO.city}": "Paris",
"${GEO.country_name}": "France"
}
}
}
}
RESTful API Route
Manage users and roles governance rules programmatically through AAM's RESTful API endpoints. This allows deeper integration with custom services. Refer to the "Users & Roles Governance" page for available API endpoints, or download our Postman collection for pre-made API calls.