Underestimated aspect of API access controls
With the rise of the WordPress RESTful API, plugin and theme developers are incorporating custom API endpoints to enhance website functionality. While the WordPress core team has implemented security measures and provided guidelines for protecting API endpoints, not all developers adhere to these recommendations. Moreover, even when API endpoints are properly secured, they remain easily discoverable, potentially enabling malicious actors to gather information about the plugins used on your WordPress website for intrusion planning.
Understanding WordPress RESTful API discovery
Let's conduct a quick experiment. Open your preferred web browser, enter your WordPress website's domain, and add the /wp-json prefix to the URL. If your website has the RESTful API enabled, you'll witness a wealth of data loading on your page.

This raw data represents your entire RESTful API landscape, which could be exploited by cyber-criminals to ascertain your API endpoints, installed plugins, and formulate attack strategies.
Protect RESTful API
There are two primary methods to safeguard your RESTful API endpoints with Advanced Access Manager (AAM) plugin:
- "API Routes" service. The first approach entails utilizing the "API Routes" service offered by the AAM plugin. This service provides an easy-to-use user interface that allows you to selectively protect individual endpoints. With this method, you can handpick which API endpoints require additional protection. It offers a granular level of control over your API security.
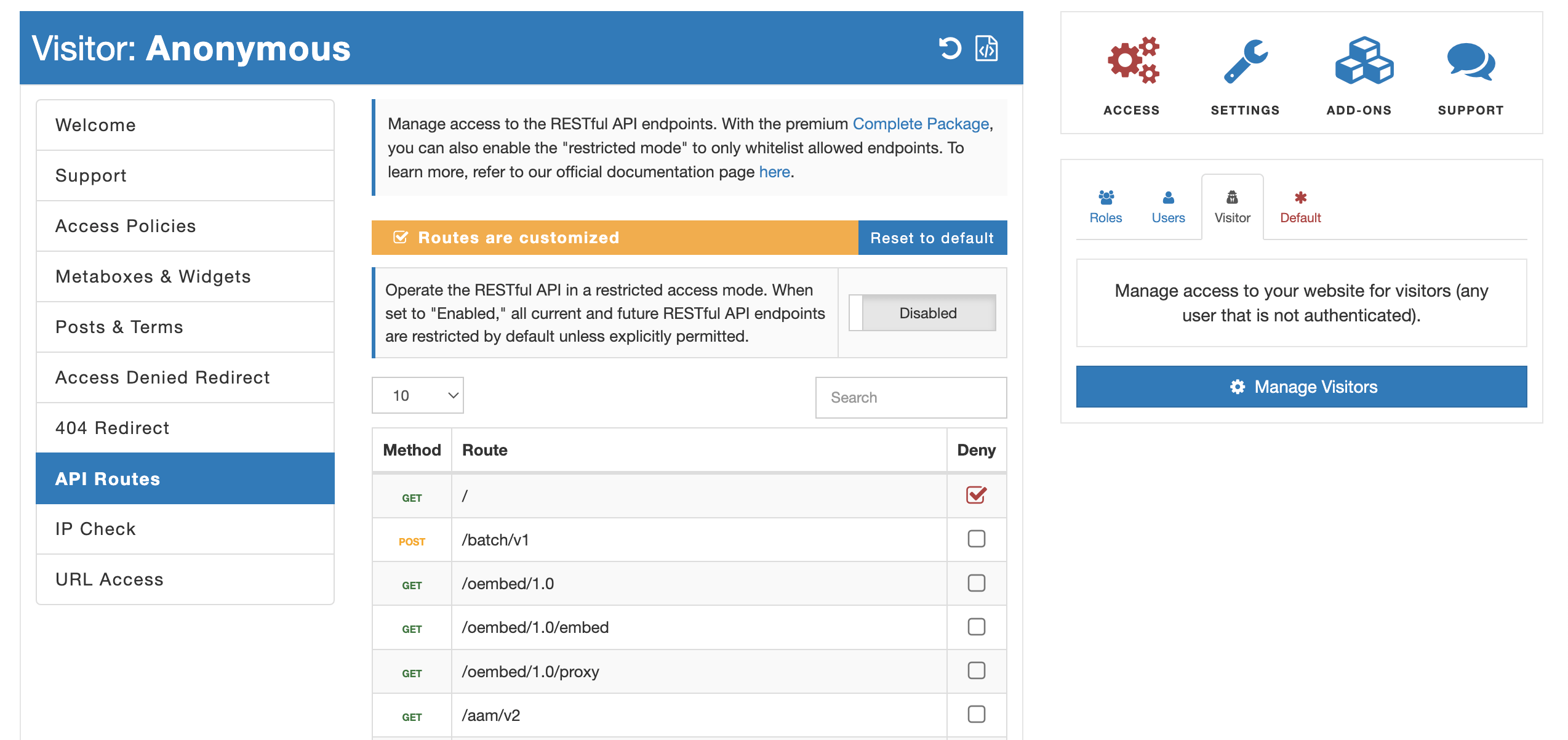
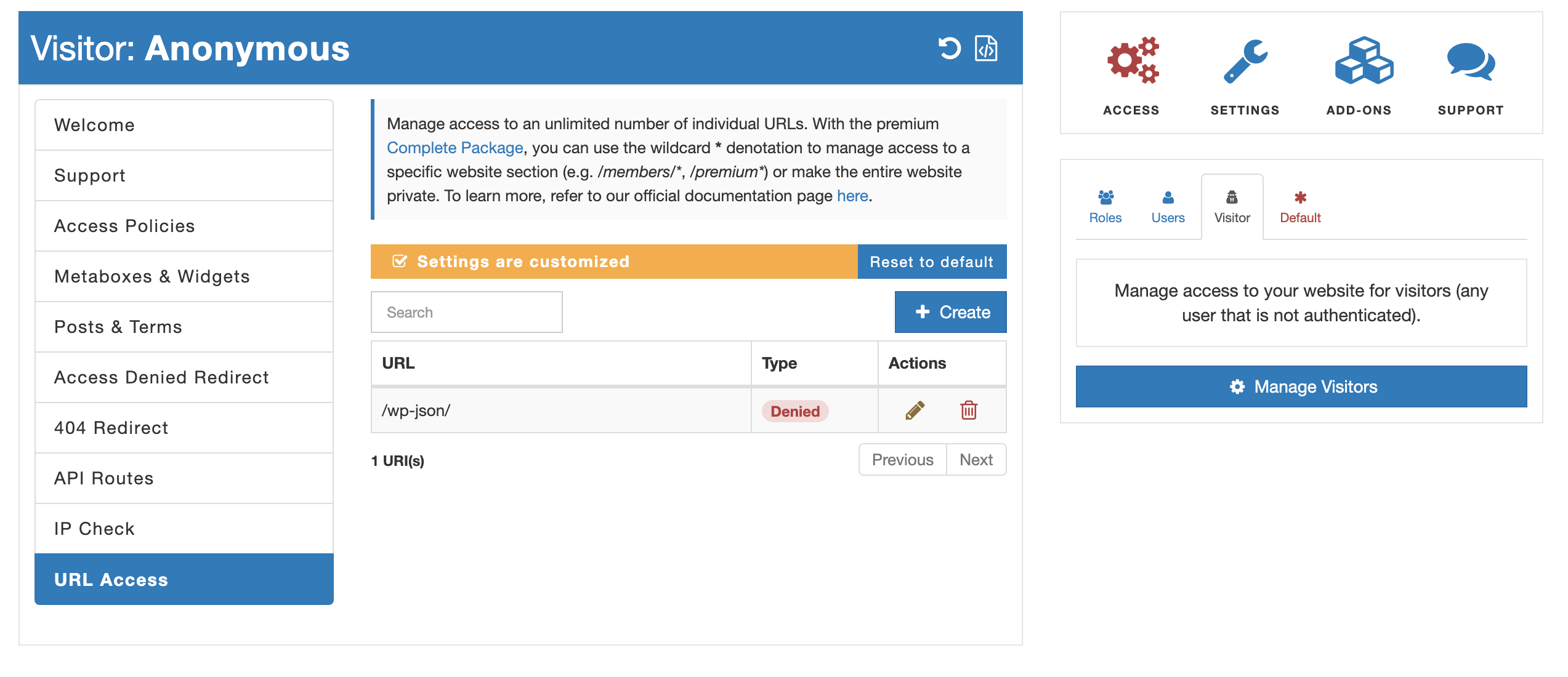
- "URL Access" service. Alternatively, you can employ the "URL Access" service provided by AAM. Since each RESTful API endpoint is essentially a URL, this service allows you to apply protection at the URL level. The key difference between this and the "API Routes" service lies in the level of control, as "API Routes" takes into account HTTP methods such as POST, GET, DELETE, etc.
Old-School XML-RPC
It's essential not to overlook the legacy WordPress XML-RPC API, which remains available within WordPress and could serve as an attack vector. While the majority of existing plugins and themes no longer support this API, it's unlikely that your website requires it. As a precautionary measure, you can safely deactivate the XML-RPC WordPress API by navigating to the AAM "Settings" page under the "Core Settings" tab. Here, you'll find the option to disable this API, further bolstering the security of your WordPress website.
Conclusion
Securing your WordPress RESTful API is crucial in preventing unauthorized access and potential attacks on your website. By following the recommended security measures, such as those provided by the Advanced Access Manager plugin, you can protect your API endpoints and reduce the risk of malicious exploitation.
Additionally, deactivating legacy components like the XML-RPC WordPress API adds an extra layer of security to your WordPress site, ensuring a safer online presence. Stay vigilant and proactive in safeguarding your website from potential threats in the ever-evolving digital landscape.