Securing WordPress RESTful API endpoints
In the ever-evolving landscape of web development, the need for robust security measures has never been more crucial. One area where security vulnerabilities can often be found is in the realm of RESTful API endpoints, especially within popular content management systems like WordPress. These endpoints, often used by plugins and themes, can inadvertently expose your website to potential threats if not managed carefully. In this article, we will explore the importance of defining default access to RESTful API endpoints and how to restrict them unless explicitly allowed, all while safeguarding your WordPress website with the Advanced Access Manager (AAM).
The challenge of unrestricted RESTful API
Modern WordPress plugins and themes frequently incorporate custom RESTful API endpoints to enhance functionality and improve user experience. These endpoints, however, are often easily discoverable through the /wp-json/ URI, making them accessible to anyone with a basic understanding of web development. The open accessibility of these endpoints can lead to various security risks.
One significant issue arises from the fact that not all developers adhere to WordPress security best practices when creating these endpoints. Some may inadvertently expose sensitive data or functionality to unauthorized users, creating a potential entry point for hackers. This vulnerability can result in a compromised website, data breaches, or other security incidents that can harm your online presence and reputation.
Mitigating the risk with AAM
To address the critical issue of securing RESTful API endpoints, the Advanced Access Manager (AAM) offers an effective solution. AAM empowers WordPress website owners and administrators with the ability to enable restricted mode for the entire RESTful API, allowing only those endpoints that are explicitly needed for the site's operation.
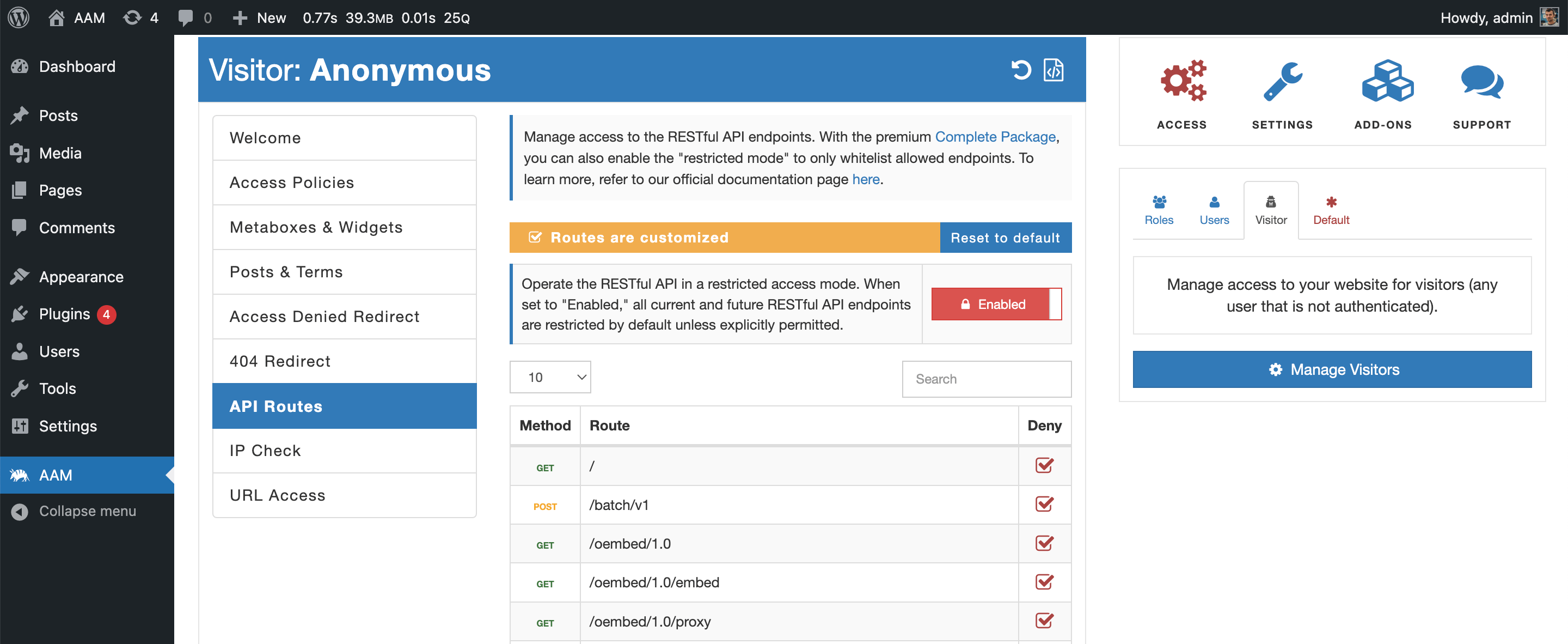
Here are the key features and benefits of AAM's RESTful API access control:
- Default Access Controls. AAM enables website owners to establish a default access control policy for all RESTful API endpoints. By setting a default policy of "restricted," you ensure that no endpoint is accessible by default unless explicitly allowed.
- Granular Control. AAM provides granular control over individual RESTful API endpoints. Website administrators can specify which endpoints are permitted and which ones should be restricted, aligning with the website's security and functionality requirements.
- Improved Security. By restricting access to only essential API endpoints, AAM significantly reduces the attack surface of your WordPress website. This proactive approach enhances your website's security posture and minimizes the risk of potential breaches.
- Compatibility. AAM is designed to work seamlessly with a wide range of WordPress plugins and themes. You can confidently use popular plugins while ensuring that the associated RESTful API endpoints are appropriately controlled.
- Easy Configuration. AAM's user-friendly interface makes it easy to configure RESTful API access control settings. Even users with limited technical expertise can efficiently manage and secure their website's API endpoints.
Conclusion
In a digital landscape where security threats are constantly evolving, taking proactive measures to protect your WordPress website is paramount. Securing RESTful API endpoints is a critical aspect of website security, as these endpoints can be exploited if left uncontrolled. The Advanced Access Manager (AAM) offers an effective solution to mitigate this risk, allowing you to define default access policies and restrict access to RESTful API endpoints unless explicitly permitted.
By leveraging AAM's features, you can enhance your website's security, maintain control over its functionality, and safeguard sensitive data from potential threats. With AAM, you have the tools to confidently manage your WordPress website's RESTful API endpoints and protect it from unauthorized access and potential security breaches. Stay ahead of the curve in website security by implementing AAM and fortify your online presence against emerging threats.